The Road To The Quantum Internet Era v2.0
What is the role of Post-Quantum-Cryptography?
Welcome back to OneQuantum Libya, your go-to source for all things quantum in Libya, and yes it’s been quite a time since the last issue. In our previous edition of "The Road to Quantum Internet" series (click here) we explored some developments and challenges in the exciting world of quantum networking.
At this point, we will shift our focus to a crucial aspect of quantum security: post-quantum cryptography (PQC). As quantum computing becomes increasingly powerful, traditional cryptographic techniques will no longer suffice. PQC offers a solution by using algorithms that are believed to be resistant to quantum computing attacks.
It's important to remind the reader that PQC is not the only solution for quantum security. Quantum key distribution (QKD) is another ultimate securing solution that offers hardware-level security. While PQC focuses on software-level security, it's essential to have both QKD and PQC solutions in place to achieve optimal quantum security.
In this issue, we'll explore the necessity of implementing PQC, how to start implementing pilot projects, examples of successful PQC implementation projects, and the latest developments in PQC efforts. Let's dive in.
Breaking The P-Q-C Into Simple Terms

Post-quantum cryptography, also known as quantum-resistant cryptography, is a field of cryptography that deals with cryptographic algorithms that are secure against attacks by quantum computers. Quantum computers use the principles of quantum mechanics to perform certain types of calculations much faster than classical computers. This means that they can easily break many of the classical cryptographic algorithms that are currently in use.
The main goal of PQC is to provide cryptographic algorithms that are secure against attacks by quantum computers. These algorithms are designed to withstand the power of quantum computers and to ensure the confidentiality, integrity, and availability of sensitive data. PQC methods are fundamentally different from classical cryptographic methods. While classical cryptographic methods rely on the difficulty of solving mathematical problems, post-quantum cryptographic methods rely on different mathematical problems that are believed to be hard even for quantum computers.
Why Organizations Should Adopt PQC
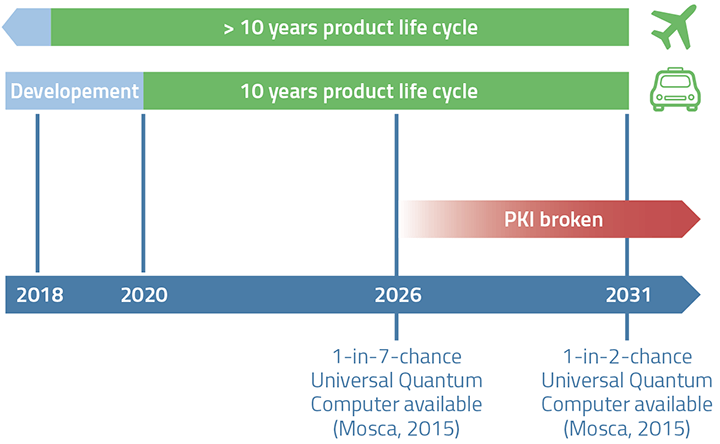
Organizations should start adopting PQC for several reasons. First, it provides long-term security for sensitive data. With the rise of quantum computing, traditional cryptographic methods may no longer be enough to protect sensitive data. Adopting PQC can future-proof organizations against the potential threat of quantum computers. While quantum computers are not yet powerful enough to break most of the classical cryptographic algorithms in use today, it is widely believed that they will become powerful enough in the near future. By adopting post-quantum cryptography, organizations can ensure that their sensitive data remains secure even as quantum computers become more powerful.
Second, if you ask around, most of the security specialists would agree that it takes quite a time to migrate the network infrastructure with new cryptography schemes that protects the network nodes. Thus, companies that govern the telecom infrastructures should start now rather later on establishing pilot projects and test-beds for several reasons (not limited to):
Understand how PQC schemes can be accredited and what resources are needed to transition to these schemes.
Demonstrate and estimate the time needed to migrate the network with PQC.
Define the required skills that are get the job done.
Third, adopting PQC can enhance trust with customers and partners. By adopting the latest and most secure cryptographic methods, organizations can demonstrate their commitment to data security and protect their reputation in the event of a data breach. On the other hand, failing to adopt post-quantum cryptography could lead to significant financial and reputational damage in the event of a data breach.
How to Implement PQC Pilot Projects
Post-quantum cryptography is a relatively new field of study, and many organizations may not know where to start with implementing PQC in their systems, we will briefly discuss the technical aspects of PQC implementation, including the steps needed to develop and test PQC algorithms.
The first step in implementing PQC is to determine the specific use cases for PQC in your organization. This will help identify the necessary PQC algorithms and determine how they will be integrated into existing systems. The next step is to choose a PQC algorithm that meets the needs of your use case. There are currently several PQC algorithms under development, and organizations should consider factors such as the algorithm's security, performance, and ease of integration when choosing a PQC algorithm (much more about this aspect in the future newsletter issues).
Once a PQC algorithm has been selected, the next step is to develop and test the algorithm. This involves coding the algorithm, testing it for security vulnerabilities, and verifying its performance. Organizations can use open-source PQC libraries, such as pqcrypto or liboqs, to help with the development and testing process. These libraries provide a set of tools and functions for implementing PQC algorithms and can save organizations time and resources in developing their own PQC solutions. Yet, this does not exclude that companies and organizations still need a help of specialist in post-quantum, to assess the algorithms demonstration and migration.
After developing and testing the PQC algorithm, the next step is to integrate it into the organization's existing systems. This involves modifying the systems to incorporate the PQC algorithm and testing the systems to ensure they are functioning properly. Organizations should also consider how to manage the keys used for PQC, as key management is critical for ensuring the security of PQC systems.
PQC Implementation Projects & Resources
To inspire and guide readers, let’s showcase real-world examples of PQC implementation projects. These projects demonstrate how PQC can be implemented in different use cases and industries.
Recently, the National Institute of Standards and Technology (NIST) released its third-round candidates for PQC algorithms. This marks an important milestone in the standardization process for PQC and offers a variety of new algorithms for organizations to consider for their PQC implementations. It is worth noting that NIST has advised organizations not to implement any of the submitted algorithms until the standardization process is complete, but it is still useful to be aware of the available options.
The Singapore government's quantum-safe network for critical infrastructure is one example of a successful PQC implementation project (click here).
Hosted by National University of Singapore (NUS), the initiative will receive $8.5 million over three years with 15 private and government collaborators on board. Collaborators will bring expertise, equipment and use-cases to the project..
The network was designed to protect critical infrastructure systems, such as power grids and transportation systems, from the threat of quantum computers. The network uses PQC along with QKD to encrypt data and protect against attacks from quantum computers. The project will be providing long-term security for critical infrastructure systems in Singapore.

Members of the National Quantum-Safe Network (NQSN) team are pictured in a lab at the Centre for Quantum Technologies that will host a network node. Credits; NUS news The NATO Cybersecurity Center's quantum-proof network (click here) is an example of a successful PQC implementation project. The network was designed to protect NATO's communication systems from the threat of quantum computers. The network uses PQC algorithms to encrypt data and protect against attacks from quantum computers. The project has been successful in providing long-term security for NATO's communication systems.
The European Telecommunications Standards Institute (ETSI) Quantum-Safe Cryptography Working Group (click here): This project aims to develop standards for PQC protocols that can be used to secure critical communication infrastructures against quantum attacks. The working group has already produced several technical reports and whitepapers outlining the current state of PQC research and development.
Another important development in the PQC space is the growing interest and investment in quantum-safe cryptography by governments and industries around the world (e.g. CISA PQC Initiative). Meanwhile, major companies like Microsoft, Google, and IBM have all invested in quantum computing and related technologies, and are also exploring the development of quantum-safe cryptography solutions.
Overall, the PQC landscape is rapidly evolving, with new developments and innovations occurring on a regular basis. It is important for organizations to stay up-to-date on the latest news and updates in order to make informed decisions about their PQC implementations and ensure the security of their sensitive data in the face of potential quantum computing threats in the near future.
Conclusion
As the world becomes increasingly digitized, the need for secure communication and data storage has become more important than ever before. With the potential threat posed by quantum computers to the current encryption algorithms, organizations should start adopting post-quantum cryptography to provide long-term security for sensitive data, future-proof against the potential threat of quantum computers, and enhance trust with customers and partners. PQC adoption requires a coordinated effort from industry, government, and academia. The NIST PQC standardization process and open-source PQC libraries are valuable resources available for organizations to get started on PQC implementation.
We hope that this edition has provided readers with a better understanding of PQC and its importance for securing sensitive data, as for the upcoming newsletter issues we will dive even more in the technical and strategic aspects of implementing & migrating PQC schemes. In the next edition of "The Road to Quantum Internet Era 3.0", we will explore quantum key distribution (QKD), a technique that enables the secure distribution of cryptographic keys using quantum mechanical properties (hardware). We will discuss the basics of QKD, its applications, and the challenges associated with its implementation. Stay tuned!
If you want to partner, or support us, please reach out to me with your goals on LinkedIn; Abdulmalek Baitulmal or email me at a.baitulmal@quanta.ly.
Sign up now for our Newsletter so that you will never miss out on quantum tech news, updates, events, and opportunities.
AbdulMalek Baitulmal | President | OneQuantum Libya
Let’s take a moment to get to know some of the Libyan landscapes;
Leptis Magna Theatre; Al-Khums, Libya


